AXLR8 have launched a free eBook about GDPR in highly regulated staffing industries. Examples include guards and security officers, close protection services, airports and care services. It is also covered by a podcast for those with time to listen, e.g. whilst travelling. The eBook is full of check lists and references. You can cut and paste them straight out. Some may be reminders for experienced professionals but many will be new. Also, there are links and references to the legal sources and template “model” agreements and policies you can use.
DPA
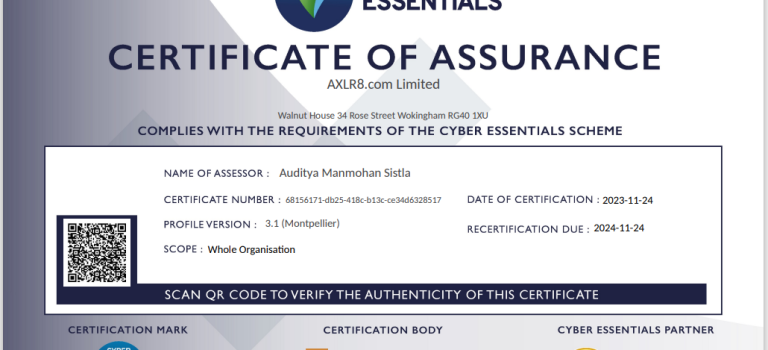
AXLR8 Cyber Essentials for 2023-4
We have just passed the Montpellier level assessment for Cyber Essentials and we are preparing for the AXLR8 Cyber Essentials Plus audit in January. Thanks again to Right Cue and IASME. This exercise is always encourages thought about our cyber security and is a springboard for the internal trainings and audits for the rest of the year.
Between now and January we are doing our annual Penetration Testing exercise. This is involves attempted hacking by skilled consultants and many vulnerability tests and infrastructure and code reviews.
Is an IRMS worth it?
AXLR8 provide special IRM systems for
- Freedom of Information,
- SARs (GDPR requests such as access or rectification) and
- EIR (requests under Environmental Information Regulations)
- Appeals
- Complaints
- Data Breaches
- and many more information governance applications.
Productivity and saving public funds
All systems purchases need to be justified financially. This article and accompanying spreadsheet explain how one can measure the difference a system makes compared to manually updating spreadsheets. That means public sector buyers can calculate how much it costs their business every month that they do not have a system!

AI developments
AI can help us with all sorts of work. We have been looking for about five years at how we could integrate the power of AI developments into AXLR8 product lines. Here are a few examples.
- Sales One simple early success came from batch OCR reading of visiting cards brought back from a trade show or trip. It works really well with competing offers from MS, Amazon, Google and others. The offers are provided on a Freemium basis. Last time we checked you could use 1000 searches a month before hitting a paywall. Nowadays, however, more utility from AI Developments when entering data into your CRM comes from customer enquiry forms on your website or AXLR8 Import Admin for, e.g. your LinkedIn contacts. Specialist suppliers are creating interesting marketing applications. We are monitoring these tools. Soon we will integrate a “best of breed” partner’s offering. Most likely, this will be for lead generation and proposal writing.
- Information Governance We researched the claims of suppliers offering AI to help with SAR redaction. Their utility did not match the claims except in the simplest examples. I would describe the results as worthy of a Khaby Lame reactions TikTok video. We will come back to that in future.
- ATS (applicant tracking systems) seems a good area for AI developments. Applying AI to recruitment strategies could really speed up onboarding staff for rapid deployments or growth. We are also looking at spotting issues with vetting and rights to work.
- Workforce planning Optimising staff journeys and bookings for shifts in security, field marketing, hospitality and counter cover seems achievable. Clients with large data sources to learn from is proving an interesting area of study.
- Finance Brokers We have seen some success with selecting funders. However, none of the AXLR8 AI developments match an experienced commercial finance intermediary professional. You need the experience and client knowledge. Like the IG example of redaction, above, there is a limit to how useful the tool an be. Also, it needs material to learn from. How much insight of a client situation is an AR prepared to type into a system. Any algorithm created by banks for loans seems to miss great funding requirements. It creates the very conditions where clients work through brokers!
- Marketing The next stage of our marketing functions would be if they autogenerated content and knew and could learn from e.g. campaign timing. Most of our clients need quality with low unsubscribe rates in their mailings. So, care would be needed. Can you spot one of our blogs that was co-written by ChatGPT?
- Systems reliability AI is most helpful behind the scenes in predictive self-healing algorithms. These fix our systems regularly before problems arise. This has been a positive AI development.
AXLR8 will carry on investing in development trials. If you feel an area of our products could be automated, please let us know.
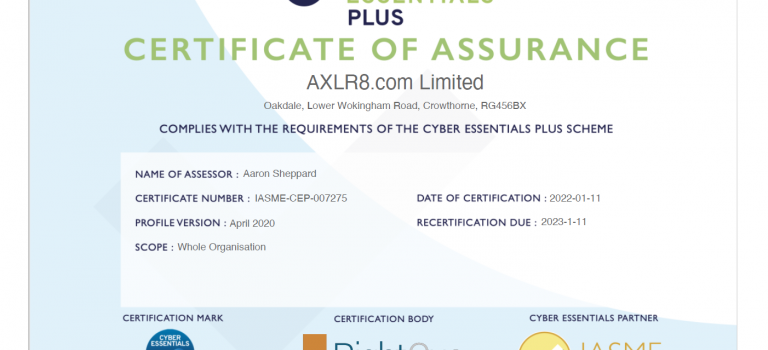
AXLR8 achieve Cyber Essentials Plus 2022-3
AXLR8 have now completed our audit for 2022-3. We are spending increasing amounts on cyber security every year. This puts AXLR8 ahead of most competitors in the markets in which we supply and support our systems.
The Journey
We would love to report that we flew through but let’s just say but the pre-audits were very useful. We are a great deal more secure again this year as a result. It will be even tougher next year as IASME are enhancing the standards. The bar is getting higher.
However, it does not just stop at the audit pass, like you we are bringing on new people and machines and constantly changing our networks for expansion. That means we need the changes to be within cyber security guidelines and we need to maintain constant vigilance with regular user tests and evidence software upgrades and security updates are happening.
Once again, we would like to thank RightCue Assurance for the audit and helpful guidance for maintaining standards in preparation for the tougher new audit in 2024.
Why should I care?
You would be concerned in a close proximity of someone coughing without putting their hand over their mouth or buying a meal in a restaurant where the chef did not wash their hands. You should be even more worried if you have a software supplier – especially as SaaS supplier – who does not maintain standards of cyber security that are audited by a reputable body. How could you trust them with your private data and mission critical system?
Please call 01344 776500 if you would like any details for this or if you are considering your own Cyber Essentials programme.

New Finance Broker Portal User Experience
Thanks to the commercial finance intermediary clients and their teams who have helped us develop and improve this new look and feel. We hope you feel we acted on your feedback and you like the results. If your organisation has not switched your user account over to it yet, here is a video showing how it works.
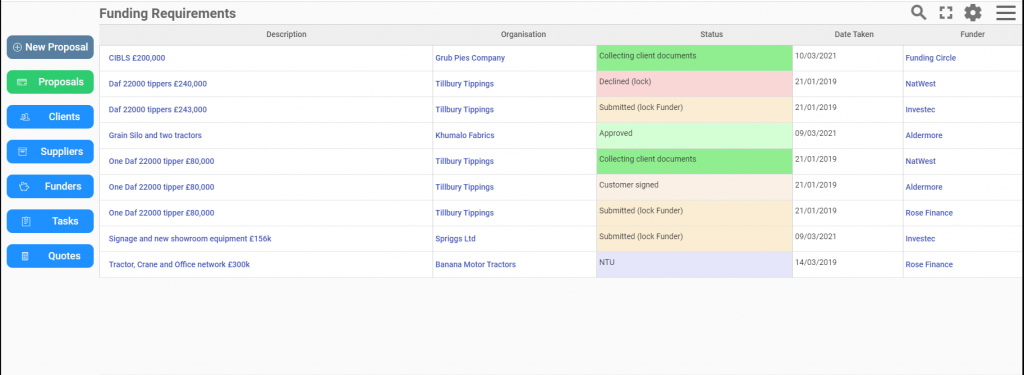
AXLR8 has been working for two years on a new set of portal development tools to create user experience (UX) – simple workflow systems that are easy to use. We have deployed them on modules of our other systems before but this is the first full systems refresh to come all the way through a year of broker feedback.
In addition to improving productivity, the new user interfaces we hope the systems are
- easy to use
- simple to understand
- quick to learn (virtually no training is our goal)
- flexible to change and evolve for your company
- easy to pick up again after a break
- friendly
- secure and quick
Please judge for yourself. Watch this video.
The new interface development tools are proven in many of our systems now including the Loan Matrix (Loan Management System), Information Asset register (IAR) and the new Talent Management and Applicant Tracking Systems (ATS) from AXLR8.
Secure Passwords
Your passwords should be unique and memorable. If you do not read any more of this article, just remember to make your passwords from three random words.
Passwords should be…
- long at least 10 characters
- unique – do not use the same password for more than one purpose
- memorable – if possible so you do not have it on a yellow sticky!
- complex – add some numbers upper and lower case characters and some non-alphanumerics such as $, -,!,@ (special characters)
- regularly changed
- securely stored if stored at all. Possibly an encrypted file or a specialist recognised password vault
- changed occasionally (changed too often can create its own security weaknesses). It is accepted that a more complex long password changed less frequently (say annually) is better than a simpler, shorter password changed frequently (e.g. every quarter).
Some of the above may conflict. The better (long, uncrackable, frequently changed, etc.) your password is, the more difficult it is to recall. Therefore, you need to record it and, unless this is done securely, that in itself becomes a security weakness. The familiar yellow sticky on the screen is dangerous but writing them all down on a piece of paper is asking for trouble.
Only secure systems should be trusted with your personal information:
- encrypted password storage so not even the programmer of the system can read it.
- SSL encrypted browser to server communications (padlock HTTPS:// in the URL) so that it is not compromised between your PC and the server
- A ban on further attempts at password attempts after a small number of tries – five to ten attempts maximum.
Your information is probably already compromised
You must assume your password has already been found out and is available to many hackers. How? Check this site to see where your details.
Put your email into the box and see the results showing how many sites, where you used that site, and what personal information has already been stolen and has been on sale for many months or years. Everyone should know this but we reckon nineteen out of twenty AXLR8 clients we show this to are completely unaware of how exposed they are.
Brute Force Dictionary Attack
Someone can easily guess my password?
There are hacking tools that attempt thousands of username and password combinations. Many of our servers that are open to the internet have 45,000 attempts per day which are blocked.
The way password guessing works is by using information already available to the hacker’s computer. Your name is an example so do not use your name with “123” after it. Further, your first & last name, school and many more pieces of personal information must be assumed to be known by hackers. If you have a word that is typically used in your password such as a pet name, animal, flower, place, or whatever, a “Dictionary” attack will probably find it by using a list of common words and configurations of those words. For example, Dictionary attacks are really good at words and phrases. They also check adding your date of birth and other information they have derived or purchased. Thus, if your password is made from the word Banana and your date of birth (in this example 10th November), you might make a password like “B4n4n4-1011” On the face of it, this is more than 8 characters and obeys many of the accepted rules from a few years ago.
Good dictionary attacks already have your date of birth, first pet’s name, primary school name, and many other answers to “hint” and “ID check” questions you might have entered in other sites as mentioned above. Most know dates of birth and names of children, which are very common combinations for passwords. All know combinations of common passwords like “Secur1ty”, “pass1234”, “Password!” and “letmein” is well known. Similarly, although it is not the subject of this article, please do not keep your default firewall or blue tooth PIN as “1234” or “0000”. Also, obviously, do not make it the same as your bank PIN!
Yikes! What shall we do then?
Password reset
You should change your password now.
Dictionary attacks are very, very good at finding a word or phrase and number combination. However, they are unable to begin to guess at something you passed on the way to work, a randomly selected object in your house and a film you like or three things you saw on holiday or in a film plus your favourite actor.
Just choose three random words to make a memorable password and chuck in some number(s)/non-alpha(s) characters.
e.g. apple sock ship might end up apple1812-$hipSocks.
Maximum password attempts is a good way to protect against such attacks.
In conclusion make sure your passwords obey the rules at the top of this page and, if you do nothing else, use three random words that only you would recall because only you saw a jaguar, a robin and a bike tyre puncture on your way to the shop this morning.
Repercussions
If it is your personal password for, say a private bank, game or subscription, you may lose money or pride. Worse is possible if someone steals your identity and commits criminal offences in your name. It is not enough to know you are not guilty. There are several cases where an innocent victim of such ID theft has been attacked by another victim of the crime. Lastly, if you are at work and responsible for other people’s data on a system and neglect your duty to create a secure password and keep it secret, you could damage many other people. This could happen if you are working on any accounts, CRM, HR system and many others.
Also, if you are an AXLR8 client running a business you have built up for years, you will need to make sure that you and your staff abide by these simple rules in a complex world.
If this raises any queries, please call AXLR8 support on 01344 776500 and we can help your Super Users with your system security and staff security training.
AXLR8 Public Sector Code Library
For around five years we have asked government clients to share their code and some notes and tips every time they use AXLR8 APIs. There was a slow start but people are quite enthusiastic now.
AXLR8 are collating code samples so that public sector organisations do not have to reinvent the wheel every time a new organisation writes an interface to (e.g.) the PDL API. This should help codify a scheme that has been running for a while informally.
- Would it be helpful to see examples of other people’s code as we collect permissions from similar public sector businesses using AXLR8 APIs?
- Once finished, could we have a copy of your code for the AXLR8 Public Sector Code Library?
- Who will have access?
Just the direct programmer at the public sector organisation concerned. Reciprocation of their finished code into the PSCL will be assumed/ agreed. Programmers working for subcontractors will be asked to place their code in public ownership as a condition of participation and their employer will be copied in. Most will agree it of little cost and great benefit to all. The relevant code will be kept in our support KB and has been provided by email up to now. In future, we expect to load it on a data asset register with public sector restricted access. - Will it be a security breach?
Even if you give us the raw code, we will remove the credentials and replace them with “———”, or similar.
Even your organisation need not be identified if you wish to replace your organisation’s specific URLs with e.g. “Devshire.gov.uk” - Who owns the IPR?
I see it as Crown Copyright in 100% of cases. We have had the odd situation where a subcontractor has been less than forthcoming with the code interfacing between a public sector website and our systems and this has been one of the main motivators for this PSCL project. We have no real way to enforce this if the purchasing business do not make it a condition of the offer of work or agree perhaps a smaller fee and release the subcontractor from the obligation. However, I believe the results they achieve for such a “saving” will be more costly in the end and less maintainable. - What else do we need?
It would be helpful to others to say what CMS your system works with and provide any other notes. Perhaps some notes on what you might have done if you had more time? - What if my code was not as clean as I would have liked due to the time I was given?
Your code is brilliant. Do not worry, it will help someone and all devs know they have done the same somewhere.
Any questions or comments, please contact AXLR8 Support on 01344 776500.
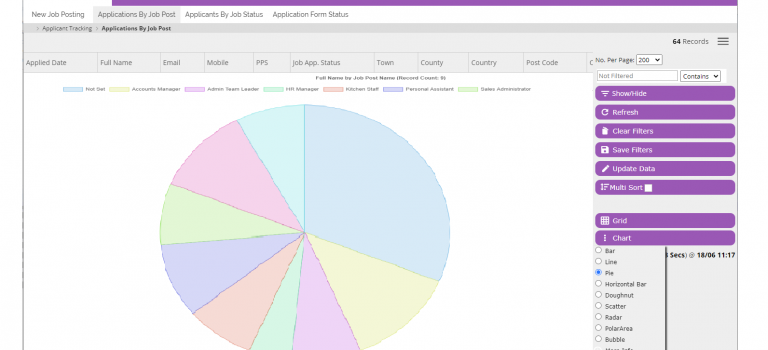
Clear new AXLR8 Portal interfaces
AXLR8 has been spending the last three years updating and improving the AXLR8 User Experience (UX). Many parts of the system are now being systematically added and seamlessly replacing exisiting client systems.
Staffing Agencies
Field staffing apps have been evolving for a while and are now customised to your company and also have all the functionality you would expect from AXLR8’s comprehensive staffing agency systems.
The staffing systems internal HQ Admin wokflows are being improved, functon by function, starting with the recruitment team using AXLR8 applicant tracking systems.
Dashboards
AXLR8 Dashboards are built internally at clients with knowledgeable accredited AXLR8 Super Users now. They can be built and placed any where in the system but the most popular place is the opening page with a management overview.

Finance
AXLR8 are growing in the commercial finance and loan management systems markets as a direct result of improving user interfaces.
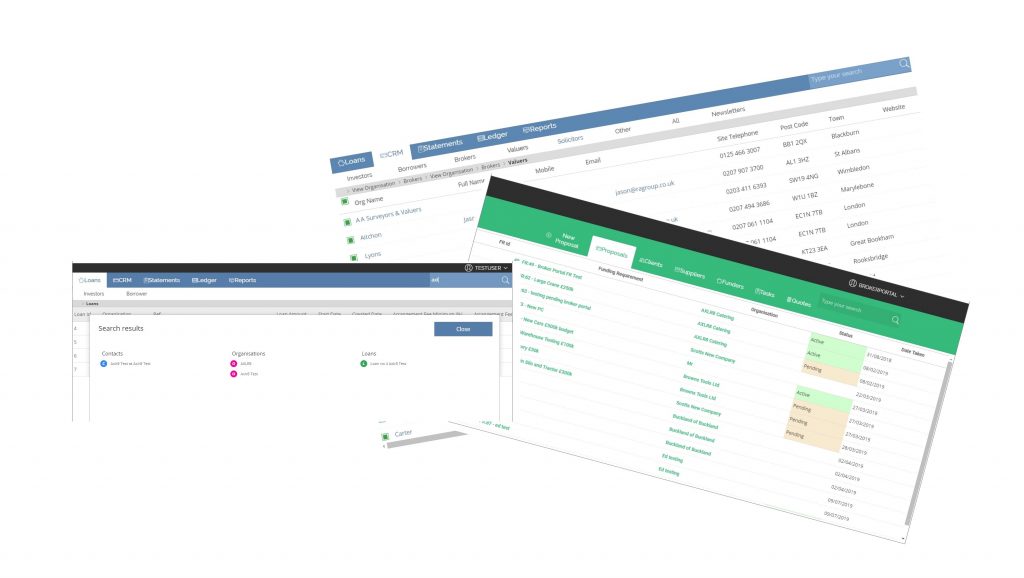
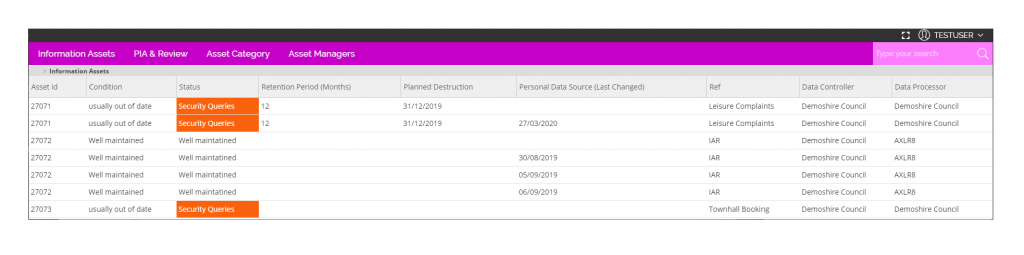
Government
AXLR8 is updating the Information Request Management and Information Asset Register systems in use across central and local government and NHS.
Apps
AXLR8 have been delivering Apps on all major operating environments for seeral years for our clients to replace and complement our web apps and web portals.

The above maintenance app is a simple “see snap send” reporting mechanism as well as containing all the information requied for service, installation and other equipment management tasks for an engineer.
The comprehensive AXLR8 Staffing App is simpl for the staff member to use for shift information, work planning availability calendar, pay, expenses, field reporting and surveys (on and off line) updating personal details, Chat mechanism, proof of attendance and so much more. It is used by tens of thousands of staff every day.
Please email sales@axlr8.com or call us about your business systems requirement 01344 776500
AXLR8 Login Tips
Security is only going to get stronger in the world of business applications.
Therefore, some of your legitimate users will face occasional barriers to accessing your business applications including the one you have purchased from AXLR8.
Quick fixes
Assuming they are legitimate users, the quick solutions you can try are as follows.
| Common user issue | What to do about it |
| Forgot password (includes typing the wrong case e.g. “ABCD1234” instead of “AbCd1234”) | They should go through the password reset process. It sends them a temporary login and instructions on how to create a new secure password. A Super User can also kick off this password reset process. |
| Too many false login attempts | The users account will be disabled. A Super User needs to go to their User Admin area, select that user and take their account from the “disabled” to the “active” list. Don’t forget to check they are still legitimate users! |
| Not received password reset email | The email with the reset password instructions has probably gone into their spam folder.* The user must check their spam folder, retrieve the mail and follow the instructions. |
| User forgot login name (includes typing it wrong such as “JOHN SMITH” when it is actually “JOHNSMITH” without a space) | They can use the user name reminder process. You can send them the correct user name and explain the importance of typing it exactly. |
*If all go to spam, then your DKIM and SPF records a may not be set up correctly and you may need to ask assistance of whoever manages your DNS. AXLR8 can re-supply the correct values for these.
The above should solve it (and probably similar problems from any system you may use, from any supplier). If not, one of your company’s AXLR8 Super Users should follow the steps in the link below with your user (client, field staff, etc.) in order to resolve the matter.
Detailed help notes
For more detailed instructions about how to troubleshoot problems when users cannot log in, please click here.
