The short answer is email security delivery and spam prevention which are related in many ways. Do not ignore these seemingly boring acronyms: DKIM and SPF. They help us assess whether we can trust emails.
What is the problem?
Opening every email is a risk. You need to trust emails you open. You need recipients to trust the ones you send.
One way to reduce that risk is to know who has sent it and assess whether or not we trust them. So how do we know who the sender is? Not by the sender name, that is for sure. Something purporting to come from a large trustworthy company, perhaps? Nat West bank or “SCREWFIX” (i.e. the tools and materials retailer) might mail you about your account or a competition. It may have come from from a different email domain if you click into it. SCREWFIX<dhlkjlj@zxyildgt .ru> is an example where you can see the “friendly name” “SCREWFIX” is completely different to the email domain name (the bit after the@-sign). See if you can spot this in the email below received as I looked for examples whilst writing this.
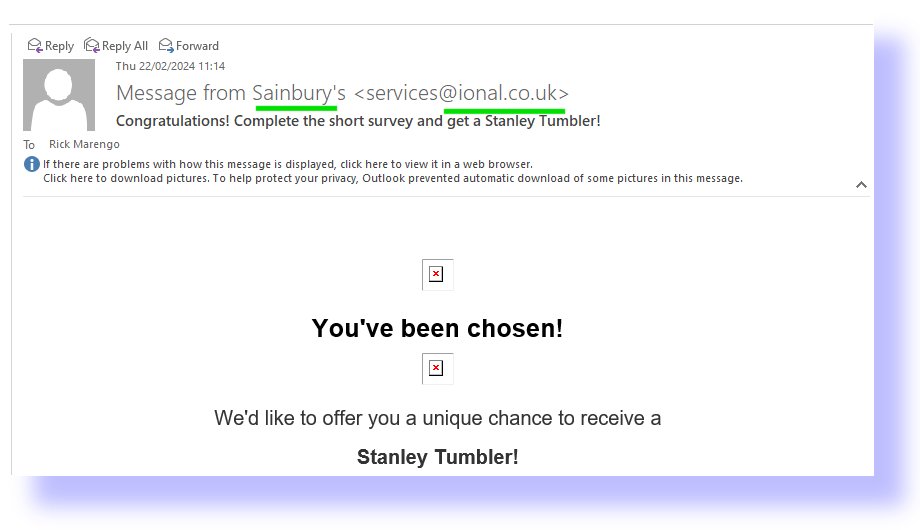
So people send emails “spoofing” that they are someone else. Much spam is probably going out from your company name right now and causing damage to your reputation. This happens to every company after a while. So, how can we be even more sure of the sender?
How do you check a sender?
Where does this email come from?
Each server on the internet has a unique “IP” address to identify it. The IP address of the server where the mail originated provides a little more assurance. You can see the IP where an email originated (and all the servers it went through before getting to your email inbox by looking in the email “headers”. Different mail programs hide this in different places but you should be able to google where it is. It is a bit like the postmark on an envelope. If it says it was posted in Leeds, and your sender lives in Leeds, you can have a bit more confidence. If it says it comes from Santa Claus and the postmark says “North Pole” any grown up knows post marks can be forged. Regrettably, an IP can be spoofed in the same way. However, there are a couple of major problems even if the IP address of the sender is completely genuine. How do you know if it is the IP of the sender or just some other IP? The answer is SPF (Spam Protection Framework).
The SPF standard allows email domain owners to say: “Email from my domain may only come from the server with this IP address and any other IP addresses should not be trusted.” That is really helpful because even if you do not go comparing the IP address from which the email originated and the IP address(es) that the domain owner has configured, the mail relays will do so. It is relatively easy for them to compare the two and many will block mails that do not comply before you receive them. Now turn it around the other way. If you do not set this up for your email domain, more and more servers will block your emails and people will not receive them. I.e., you will have a “deliverability issue”.
To add your valid originating IPs for your company, you need to add the details to the “SPF record”. This is done in the DNS control panel for your domain. The task requires technical knowledge. Do not attempt DNS changes unless you understand how it all works. Call your ISP or hosting company to ask their advice. Also, you should make sure you (or a technical manager you trust) know the access credentials for the DNS for any domain in your business so you can make changes when required.
What, When and Who are valid for this email?
Experts soon saw that the above weaknesses in SPF needed to be addressed. A new method was needed. There had to be some way machines could trust an encrypted key mechanism to see if the email was genuinely:
- sent at that date and time
- from that email address (sender)
- to that/those email addresses (recipients)
- Subject line.
This is accomplished by DKIM (Domain Keys Identification Method) whch was designed to address the problem. You need to make sure you have this set up correctly for any servers you authorise to send your email. You need to make sure your incoming email servers check it, too.
The way it works is that the email server generates an encrypted string (2048 bit is acceptable at time of writing) which encodes the above facts as the email is sent. When any mail “relay” server receives it, it can check this against a 2048 bit DKIM key that is shown publicly on the domain. If the two “fit” together, the email is passed along. If not, some other action ranging from nothing to an alert to blocking (or even deleting) takes place. Because of the challenging rise in spam and dangerous emails, the servers and mail applications are getting increasingly strict.
Once again, to set this up, you need a DNS skilled professional. The whole process should be less than half-an-hour including checking with a tool like MXToolox.com or demarcian.com. It may seem expensive and complicated but “doing nothing” is will probably come with a cost! Your business emails will get blocked and become more and more undeliverable.
You may hear about another Acronym: DMARC. (Domain-based Message Authentication, Reporting and Conformance) This is a way that email management professinals configure their servers to react to the SPF and DKIM data associated with the emails. Basically, the rules as to whether it is fine, marked a spam or so dangerous it needs to e deleted. Different professinals take different views. However, the large organisations that move the most email traffic also getting stricter. So you need to be verified byut them also or your email will be rerouted or deleted if not properly configured to prove you are who you say you are.
Verification records
In addition to the above internationally accepted DMARC standards, the major email traffic players have their own additional verification checks. If you or your clients or staff or any other stakeholders or consumers have gmail addresses or other google mail services such as G-Suite, You will need Google Verification. Ask your tech person to click here and follow the process for Google Verification. There are similar processes for other mail relay providers including Apple and Microsoft.
Some further reading
You may also wish to read this article from AccountingWeb which explains it in easy-to-understand lay terms.
Support
If you are experiencing deliverability issues sending mail from your AXLR8 system, please contact Support by email or call. We will review all of the above with you.